Apple
Three years ago, Apple introduced a privacy-enhancing feature that concealed the Wi-Fi address of iPhones and iPads upon network connection. However, recent revelations reveal that the feature has not functioned as initially described. Despite assurances that the unchangeable address would be hidden and substituted with a unique private one for each SSID, Apple devices have continued to display the actual address, which is then broadcasted to all connected devices on the network.
The issue lies in the fact that a Wi-Fi media access control (MAC) address can be utilized to track individuals across various networks, similar to how a license plate number can be used to track a vehicle’s movement within a city. In 2013, a researcher demonstrated a proof-of-concept device that logged the MAC addresses of all devices it encountered, aiming to create profiles of iPhone users based on their visited social media sites and daily locations.
In my previous article, I discussed the introduction of CreepyDOL, a distributed network of Wi-Fi sensors designed to monitor people’s movements within neighborhoods and cities. Each node, no larger than 4.5 x 3.5 x 1.25 inches, could be discreetly placed in locations like gyms, cafes, or break rooms. By sharing the Internet traffic it collected with other nodes, the system assembled comprehensive personal data including schedules, email addresses, personal photos, and current or past whereabouts of monitored individuals.
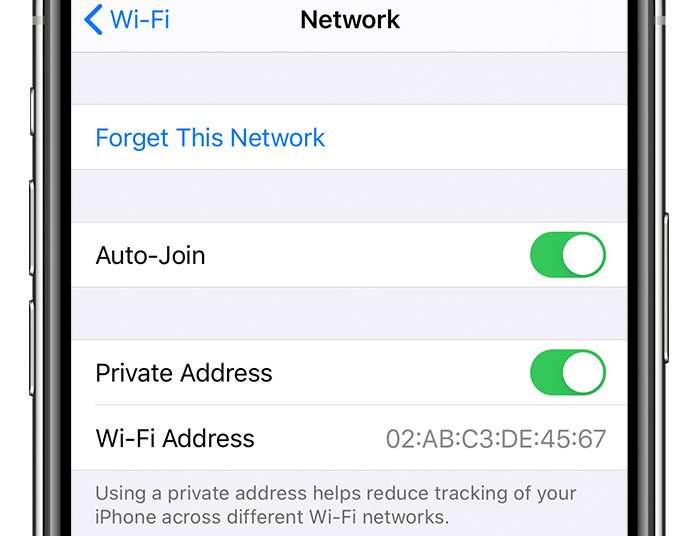
In 2020, Apple released iOS 14, which featured a default setting that concealed Wi-Fi MAC addresses upon connection to a network, instead displaying a distinct “private Wi-Fi address” for each SSID. Over time, Apple improved the feature, allowing users to assign new private Wi-Fi addresses for specific SSIDs.
On Wednesday, Apple released iOS 17.1, which included a patch for a vulnerability known as CVE-2023-42846 that disabled the privacy feature. Tommy Mysk, one of the security researchers credited with discovering the vulnerability, confirmed that the flaw had persisted since iOS version 14. Despite attempts with VPNs and Lockdown Mode, devices continued to send discovery requests with the actual MAC addresses.
Mysk shared a video demonstrating how a Mac using the Wireshark packet sniffer could monitor traffic on the local network, revealing that iPhones running iOS versions earlier than 17.1 shared their actual Wi-Fi MAC addresses on port 5353/UDP.
Upgrade to iOS 17.1 to prevent your iPhone from being tracked across Wi-Fi networks.
For most iPhone and iPad users, the impact of this revelation is expected to be minimal. However, individuals with strict privacy concerns may face real problems due to the failure of these devices to hide real MAC addresses for three years, despite Apple’s promise that the feature “helps reduce tracking of your iPhone across different Wi-Fi networks.”
Apple has not provided an explanation as to how such a fundamental flaw went unnoticed for so long. The company’s advisory for the fix simply states that the vulnerable code has been removed.