Curious about ensuring the security of your documents in the cloud? You’re not the only one. We recently received an email from Dana in Marietta, Ga., who is asking, “I just read your article on saving documents to the cloud. What is your opinion on protecting those documents by encrypting them first? Does that prevent companies like Google from harvesting them? Also, how are these files removed after the death of the individual?” – Dana, Marietta, GA
Wonderful question, Dana. Data encryption can be a complex concept at first, but when broken down, it is relatively simple. Encryption is the process of transforming data into an unreadable form that can only be accessed by authorized parties with the decryption key, which is essentially a password that can turn the data back into readable text. This makes it extremely difficult for anyone without access to steal, alter, or compromise your protected documents. Encryption is particularly useful for safeguarding sensitive files such as financial or medical documents. However, it is important to note that encryption does not guarantee complete privacy. Some companies, including Google, may have access to your encryption keys or use other methods to decrypt your data. Therefore, encrypting your documents may not prevent Google from harvesting them, depending on how you use their services and their policies.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK TIPS, TECH REVIEWS, AND EASY HOW-TO’S TO MAKE YOU SMARTER
What are the advantages of cloud encryption? The main benefit of cloud encryption is improved cybersecurity. Encrypting your documents before uploading them to the cloud adds an extra layer of protection against unauthorized access, data breaches, hacks, malware, and cyberattacks. If a data breach occurs on a site containing your encrypted information, your data will be much safer compared to unencrypted data.
Should you encrypt your data before sending it to the cloud? While most cloud services automatically encrypt your data, they typically do so in a way that may not provide the highest level of safety and privacy. These services can still access your data, and if a hacker gains access to the server, they can read your data as well. To add an extra layer of security, you can encrypt your data yourself before sending it to the cloud. Several excellent third-party encryption apps allow you to encrypt individual files or large groups of files. There are also built-in encryption methods available on both Windows and Mac operating systems. These methods can help you password-protect important documents and files, such as financial records or personal information.
How to encrypt on Windows:
1. Right-click on the folders you want to encrypt and go to properties.
2. Choose advanced under the general category.
3. Tick “Encrypt content to secure data.”
4. Click Ok and then Apply.
5. Select “apply changes to folder, subfolder, and files.”
6. Back up the file encryption key and store it safely.
If you are encrypting a single file instead of a folder, the process is just as easy. Right-click on the file, go to properties, choose advanced, tick “Encrypt content to secure data,” and follow the previous steps.
GET SECURITY ALERTS WITH THE FREE CYBERGUY NEWSLETTER – CLICK HERE
How to encrypt on Mac:
1. To encrypt folders, create a folder on your desktop and right-click to select “Create a new folder.”
2. In the top left bar, go to Go, scroll down and select Utilities.
3. Find and select Encrypting your data on a Mac.
4. In the top left bar, go to File, select New Image, and then Image from Folder.
5. Choose the folder you created and click Choose.
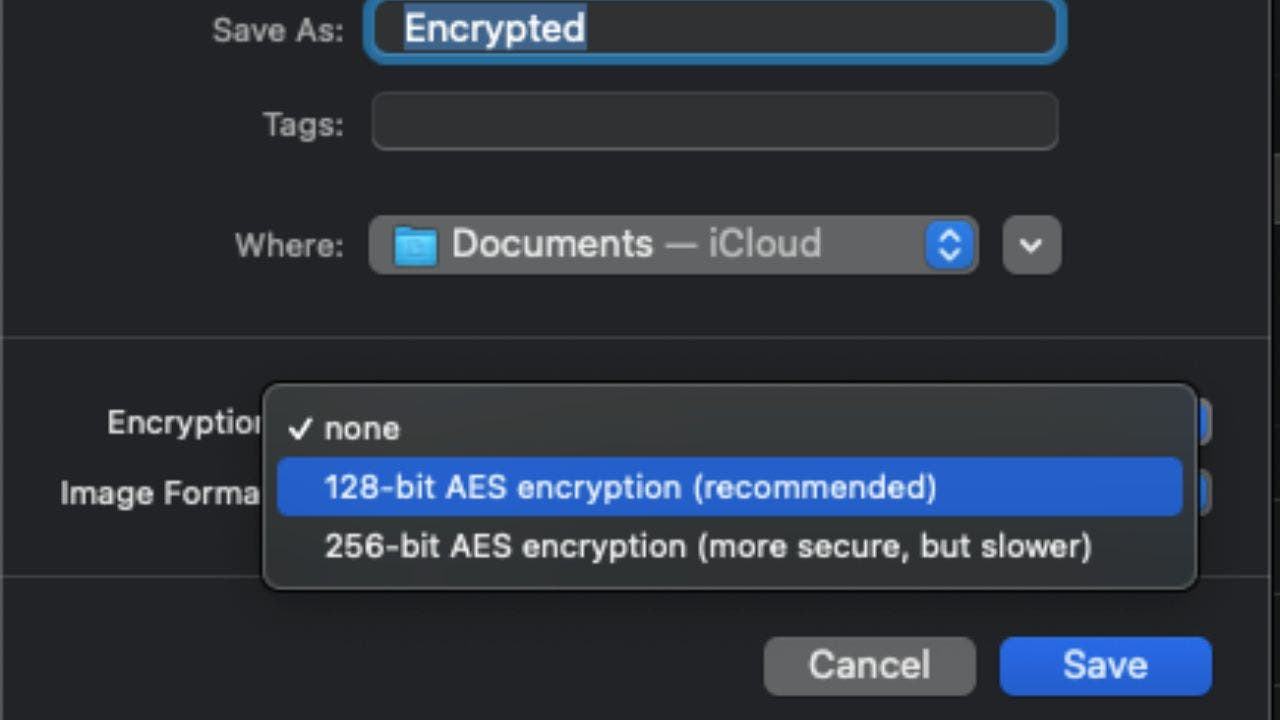
6. Select 128-bit AES encryption from the Encryption pulldown.
7. Create and verify a strong password.
8. Select the Image Format pulldown based on your needs.
9. Save and click Done.
10. Move the original unencrypted folder to the trash bin on your desktop and empty the trash.
To test the encrypted folder, double-click the encrypted file, enter the password, and open the “disk” that appears in the finder.
CRIMINAL ENTERPRISE FLAUNTS AI IN CREEPY ‘FRAUD-FOR-HIRE’ COMMERCIAL MEANT FOR DARK WEB
It is important to note that encrypting everything comes with downsides. Without the digital key, encrypted data becomes useless. Managing numerous encryption keys may be challenging, and if the key is lost or destroyed, there is no way to access the encrypted information. Additionally, while extremely unlikely, there is a possibility that an outside source may crack your encryption key. Manually encrypting data can be complicated as well.
Benefits of a password manager: To protect your data as you encrypt your documents, it is recommended to use a password manager. A password manager helps you create unique and secure passwords that are difficult to crack. It also stores all your passwords in one place, eliminating the need to remember them all. The fewer passwords you have to remember, the less likely you are to reuse them for multiple accounts. Check out my expert-reviewed list of the best password managers of 2023 here.
What to do to ensure loved ones can access your files and data after your death: Some providers may delete your files after a period of inactivity, while others allow you to designate a beneficiary or digital executor who can access your files. To enable this, be sure to share the encryption password with your loved ones.
To set up a legacy contact on a Mac, click here. To set up a legacy contact on a PC or Android, click here.
HOW TO BE REMEMBERED FOREVER ON FACEBOOK
What to do to ensure loved ones can access your files on Google after death: Google offers an “Inactive account manager” feature that automatically contacts the people you list if your Google account remains inactive for a chosen period. To set this up, follow these steps:
1. Select this link.
2. Click the pencil icon to choose the duration of inactivity.
3. Click Save.
4. Click ADD PHONE NUMBER and enter your own phone number.
5. Verify the phone number by entering the given code and click VERIFY.
6. Click NEXT.
By following these steps, you can optimize the security of your documents in the cloud through encryption and ensure that your loved ones can access your files as needed.
Denial of responsibility! Vigour Times is an automatic aggregator of Global media. In each content, the hyperlink to the primary source is specified. All trademarks belong to their rightful owners, and all materials to their authors. For any complaint, please reach us at – [email protected]. We will take necessary action within 24 hours.